서비스
모의해킹
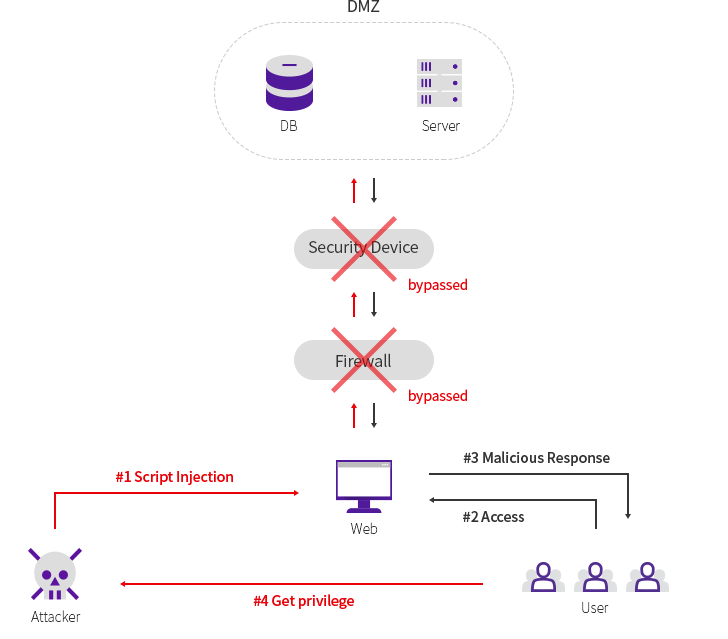
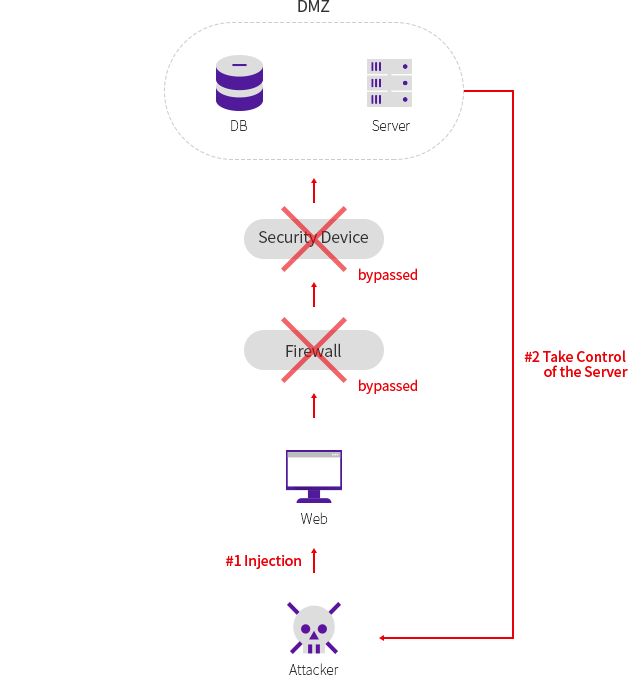
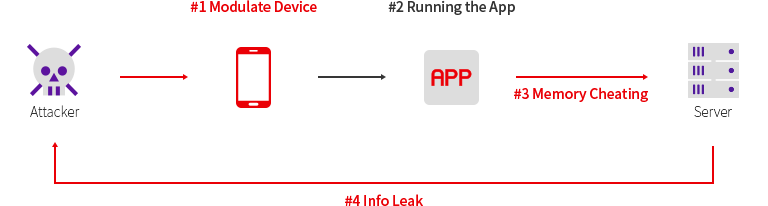
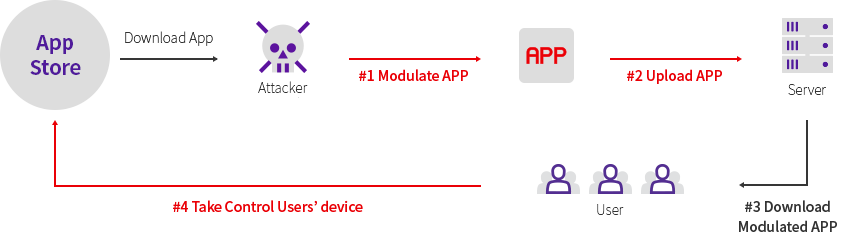
웹, 모바일, IoT, 클라우드 서비스 등 신기술이 집약된 디지털 환경에 대한 보안 취약점을 분석합니다.
실제 해커 관점에서 다양한 위협 모델 기반의 공격 가능성을 증명하고 보안 대책과 개선 방안을 제시합니다.
고급 해킹 서비스

- 글로벌 수준의 해커들 보유
-
- CODEGATE, HITB CTF, DEFCON 등 국내외 주요 해킹대회 우승 및 입상
- KISA에서 운영하는 취약점 포상제도 최우수 수상 경험 다수
- Windows Kernel, Google Chrome, Adobe, Vmware 등 글로벌 벤더사 취약점 발견 경력 보유

- 공격자 관점 컨설팅
-
- 해커가 실제 공격자 관점에서 취약점 분석
- 블랙박스 테스팅을 통한 치명적인 취약점 발견

- 다양한 진단 경력으로 검증된 수준 높은 기술
-
- 웹, 모바일, IoT, 내부 망, APT 등 다양한 경험 다수
- 금융, 대기업, 공공기관 등 다양한 분야에서 성공적인 보안 컨설팅 사례 다수 보유